Slurmrestd Access
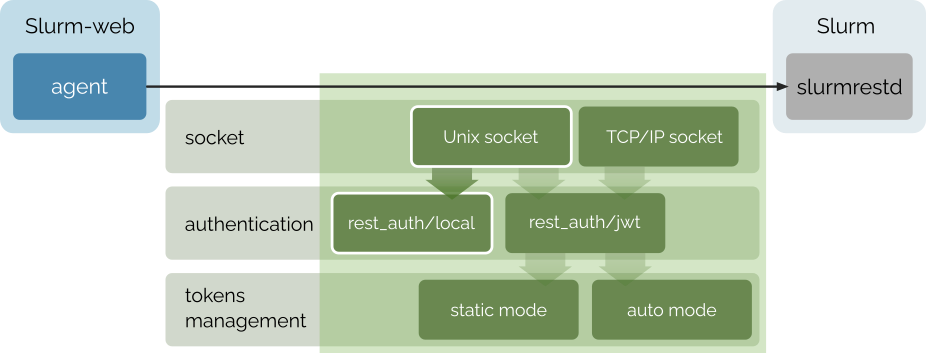
The local authentication method is deprecated since Slurm-web v5
because it requires to run slurmrestd as slurm system user which is not
supported anymore in Slurm ≥ 25.05. It is recommended to use default jwt
authentication method.
|
With local authentication method, slurmrestd service authenticates the user
with UID/GID of the client process, which must match UID/GID of slurmrestd
service itself.
In this configuration, both slurmrestd service and Slurm-web agent must run
as special slurm administrator user to get full permissions on Slurm cluster.
This is usually not recommended but it can be considered safe in this case
because Slurm-web has its own internal security
autorization policy to control users permissions and
enforce security.
Setup slurmrestd
Create /etc/systemd/system/slurmrestd.service.d/slurm-web.conf
drop-in configuration override for slurmrestd service:
[Service]
# Unset vendor unit ExecStart to avoid cumulative definition
ExecStart=
Environment=
# Disable slurm user security check
Environment=SLURMRESTD_SECURITY=disable_user_check
ExecStart=/usr/sbin/slurmrestd $SLURMRESTD_OPTIONS -a rest_auth/local unix:/run/slurmrestd/slurmrestd.socket
RuntimeDirectory=slurmrestd
RuntimeDirectoryMode=0755
User=slurm
Group=slurm
The environment variable SLURMRESTD_SECURITY=disable_user_check is
defined to force slurmrestd run as slurm administrator user.
|
Reload systemd units and enable the service:
# systemctl daemon-reload && systemctl enable --now slurmrestd.serviceSetup Agent
Edit Slurm-web agent configuration file /etc/slurm-web/agent.ini to
enable local authentication method:
[slurmrestd]
auth=localAdd permission to slurm user on Slurm-web JWT signing key:
# /usr/libexec/slurm-web/slurm-web-gen-jwt-key --with-slurm
INFO ⸬ Setting read permission on key for slurm userEdit Slurm-web agent service to run as privileged slurm system user:
-
Native service
-
Production HTTP server
With native services, edit agent service settings:
# systemctl edit slurm-web-agent.serviceAdd the following lines:
[Service]
User=slurmWhen using production HTTP server, edit agent uWSGI
service settings /etc/systemd/system/slurm-web-agent-uwsgi.service:
--- a/etc/systemd/system/slurm-web-agent-uwsgi.service
+++ b/etc/systemd/system/slurm-web-agent-uwsgi.service
@@ -5,7 +5,7 @@
[Service]
# By default, this service runs with slurm-web. When local authentication is
# used on slurmrestd, this must be changed to run as slurm system user.
-User=slurm-web
+User=slurm
RuntimeDirectory=slurm-web-agent
ExecStart=/usr/bin/uwsgi --ini /usr/share/slurm-web/wsgi/agent/slurm-web-agent.iniReload service units:
# systemctl daemon-reloadTest Access
To test Slurm-web agent and slurmrestd service configuration parameters, you
can run slurm-web-connect-check
utility. It tries to send HTTP request to slurmrestd with Slurm-web agent
configuration parameters and reports the status. For example:
# /usr/libexec/slurm-web/slurm-web-connect-check
✅ connection successful (slurm: 24.11.0, cluster: hpc)Restart agent
Upon succesful test, restart agent service to apply changes:
-
Native service
-
Production HTTP server
When using default native service:
# systemctl restart slurm-web-agent.serviceWhen using production HTTP server:
# systemctl restart slurm-web-agent-uwsgi.service